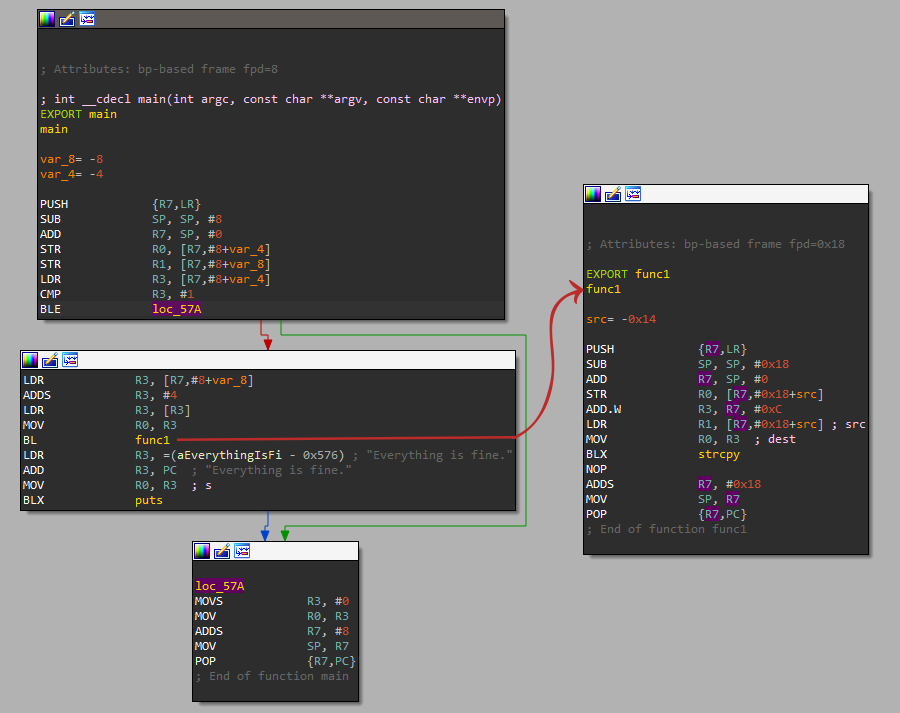
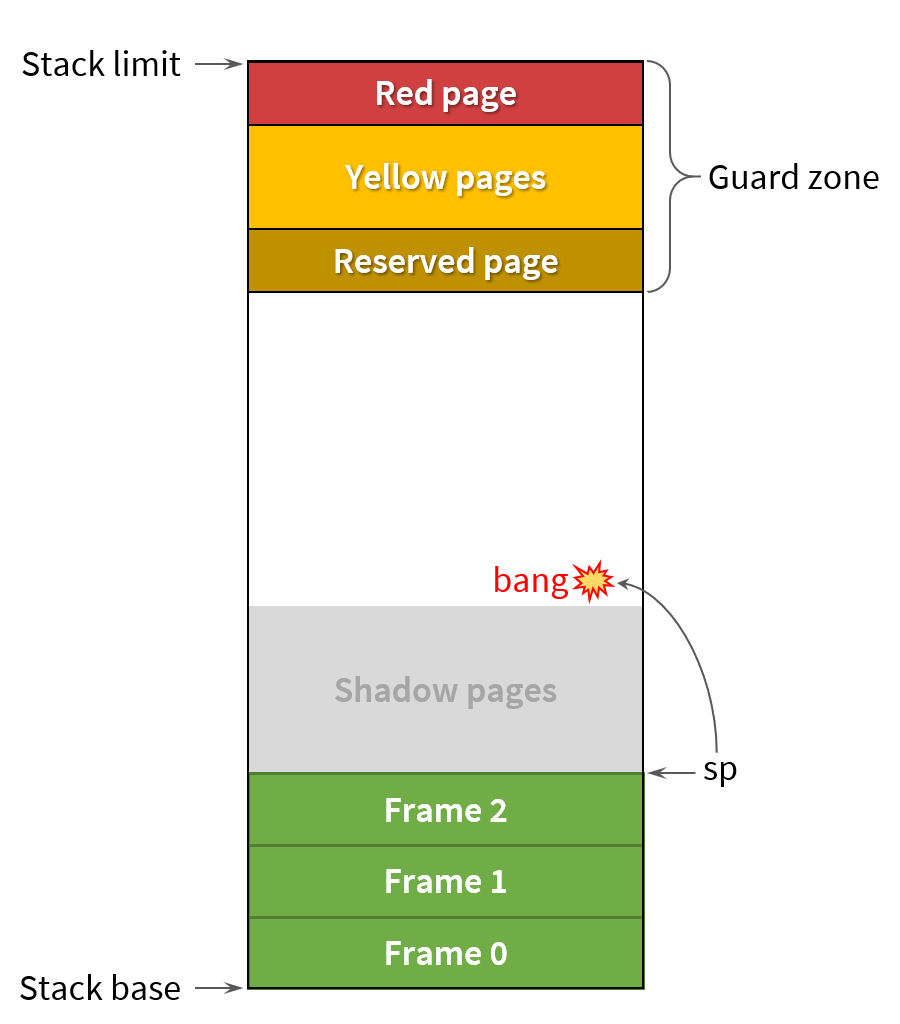
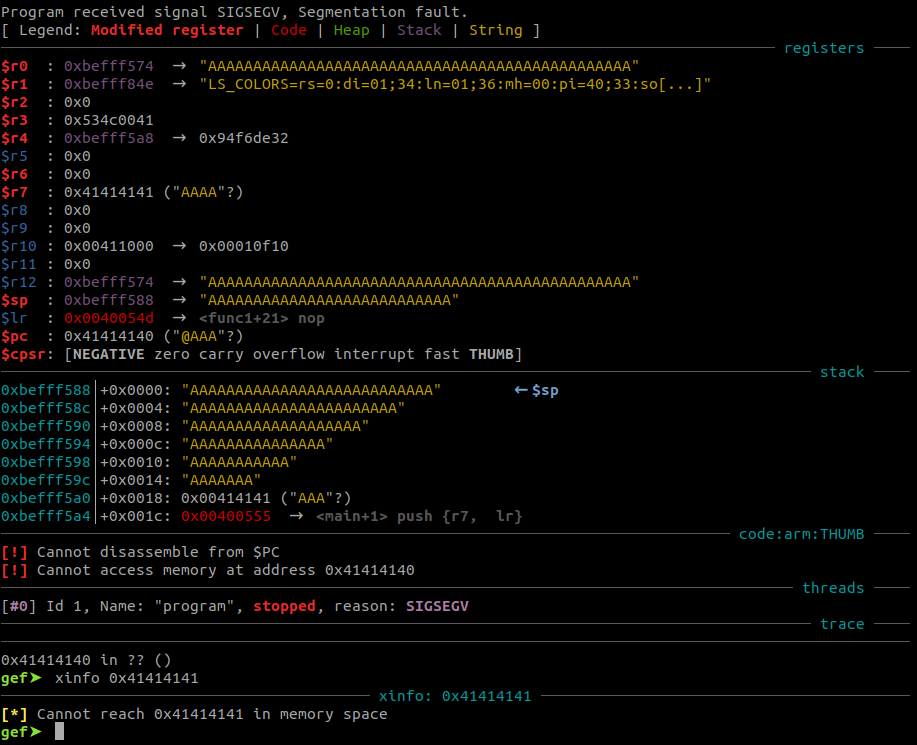
Security exploit: Hey guess what's on the stack? · Issue #2612 · Facepunch/garrysmod-issues · GitHub
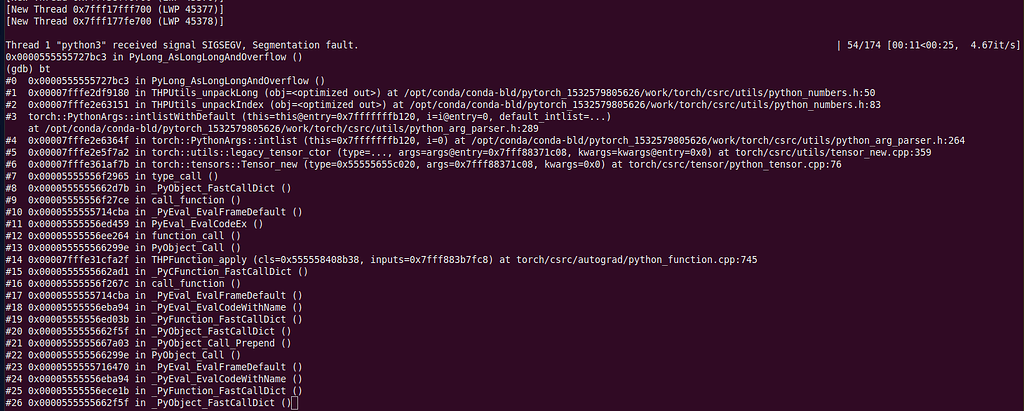
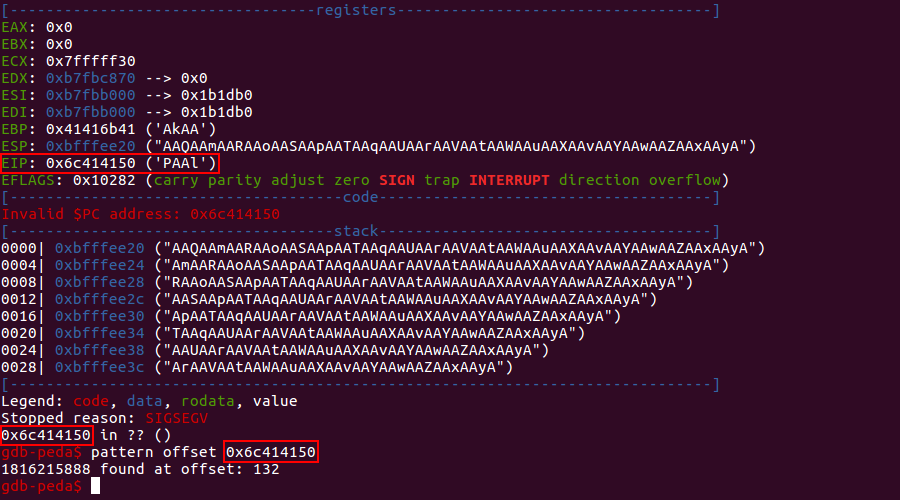
Segmentation fault when training, GDB catch event in PyLong_AsLongLongAndOverflow() - PyTorch Forums

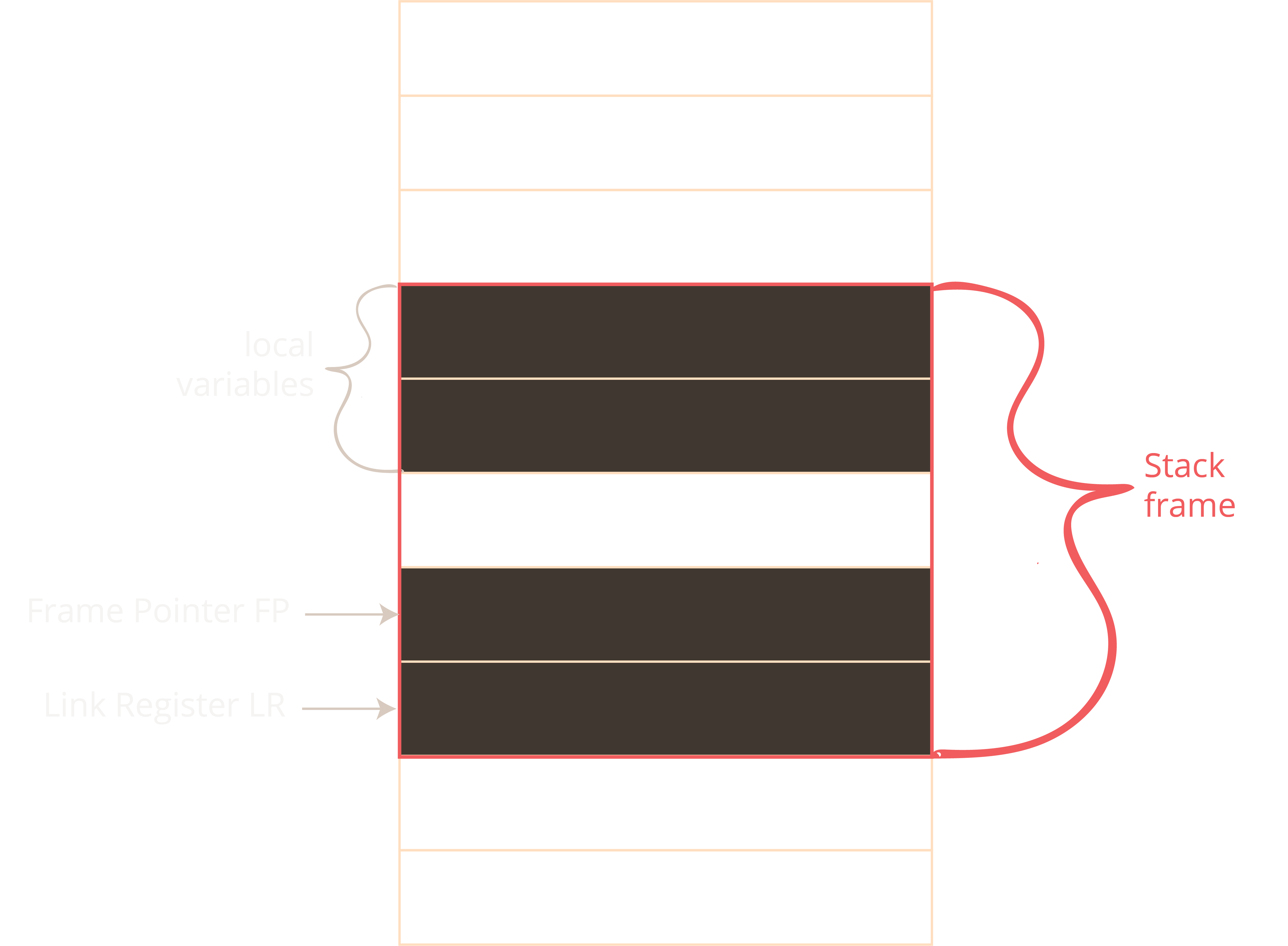
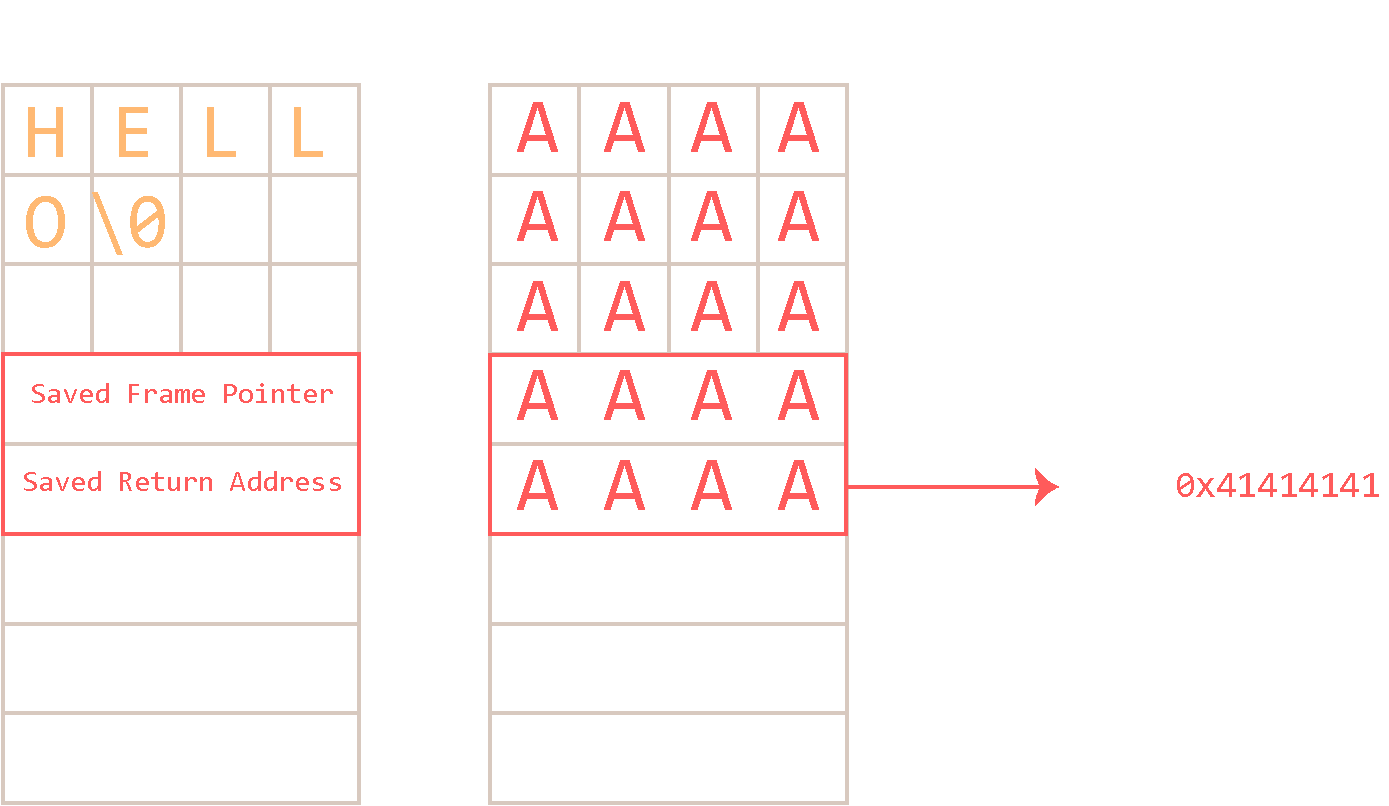
Shellcode throws sigsegv after changing return pointer with a format string vulnerability in 32-bit application running on 64-bit os : r/LiveOverflow