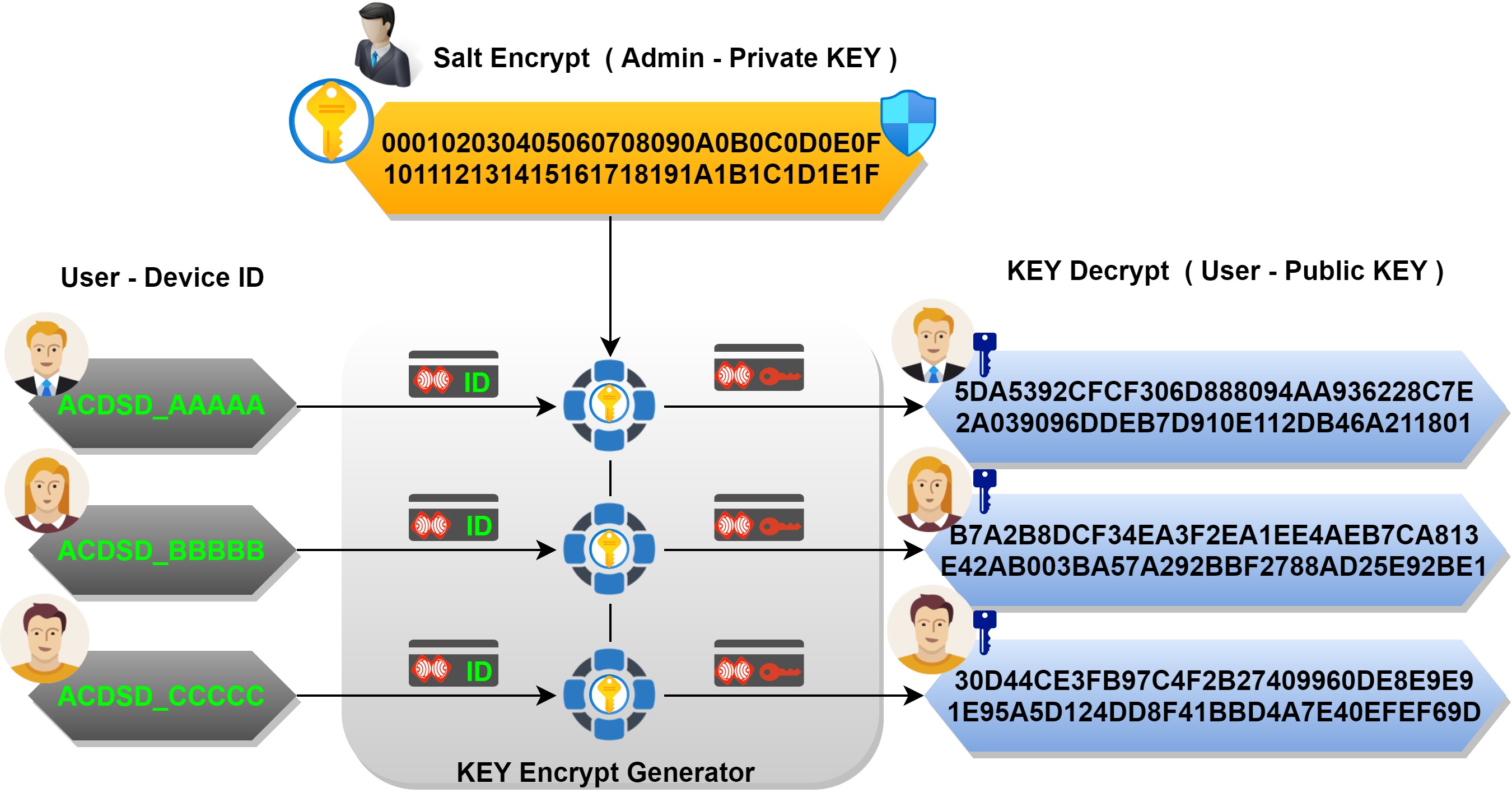
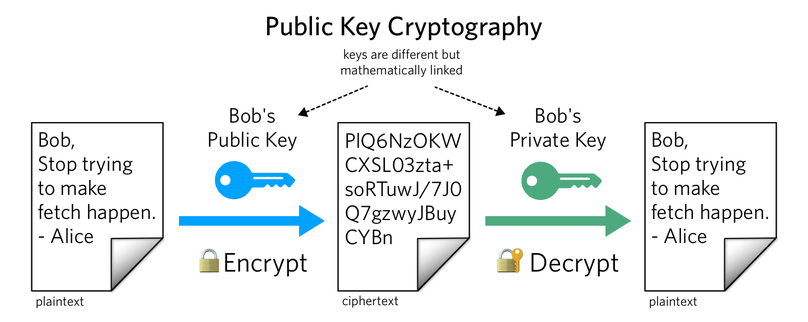
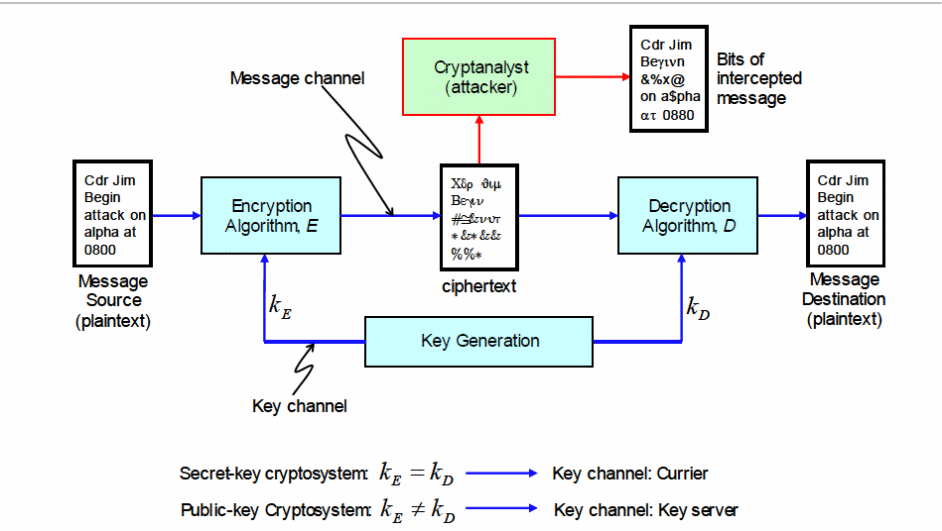
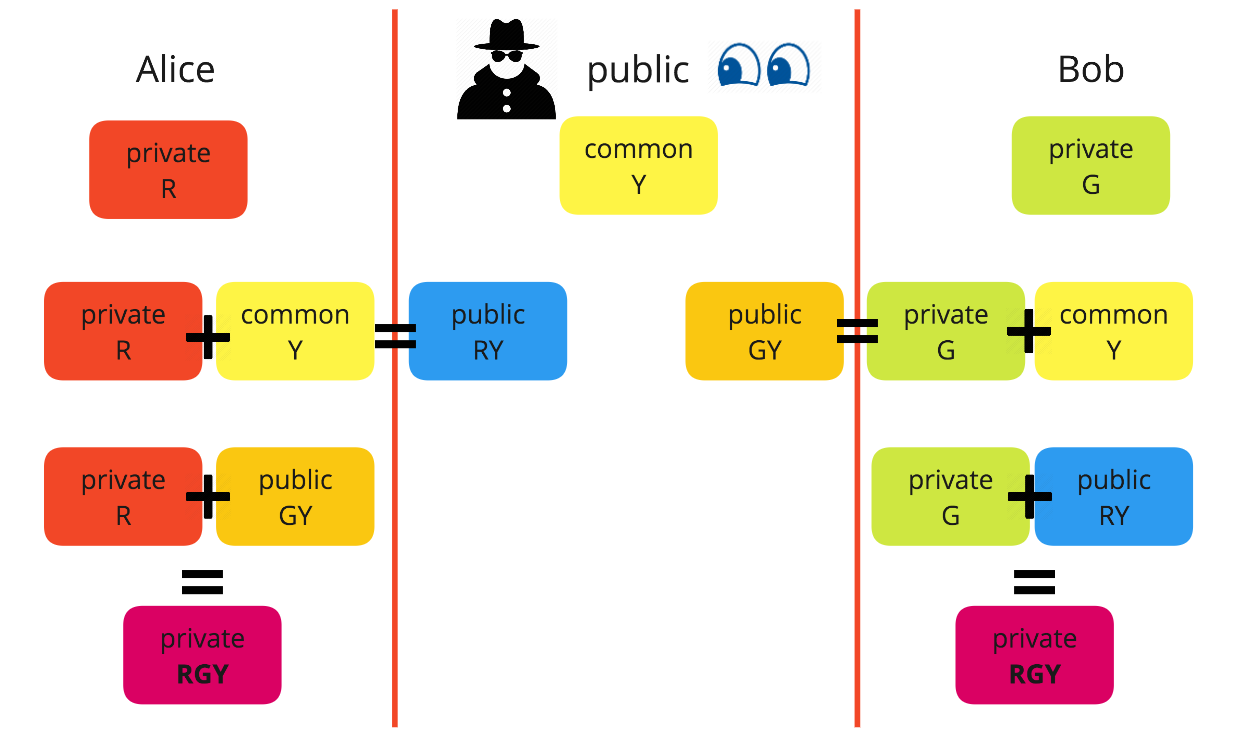
File:KG-83 Key Generator Encryption-Decryption Equipment - National Cryptologic Museum - DSC08014.JPG - Wikimedia Commons

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress
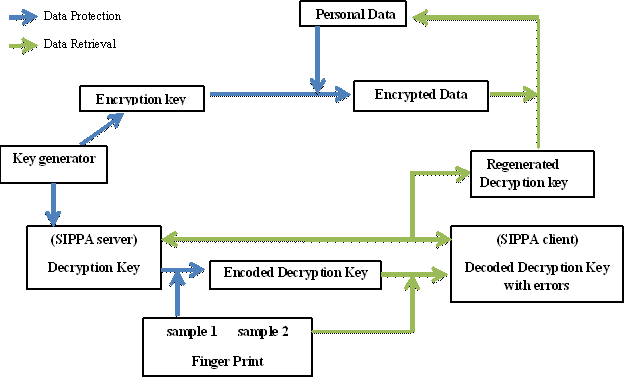
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen
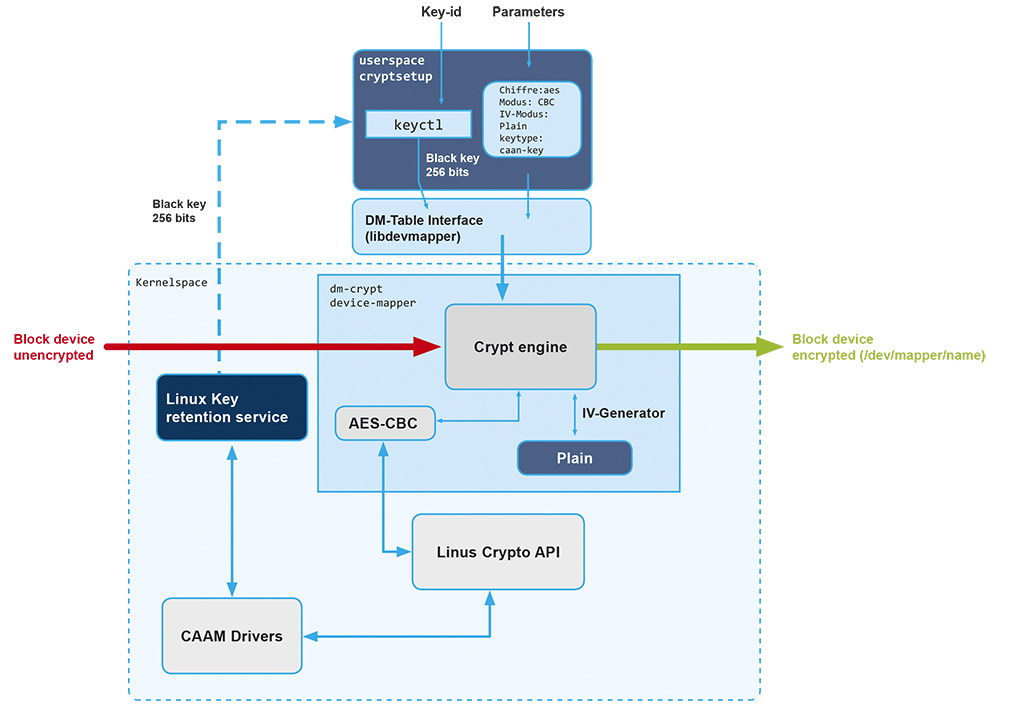
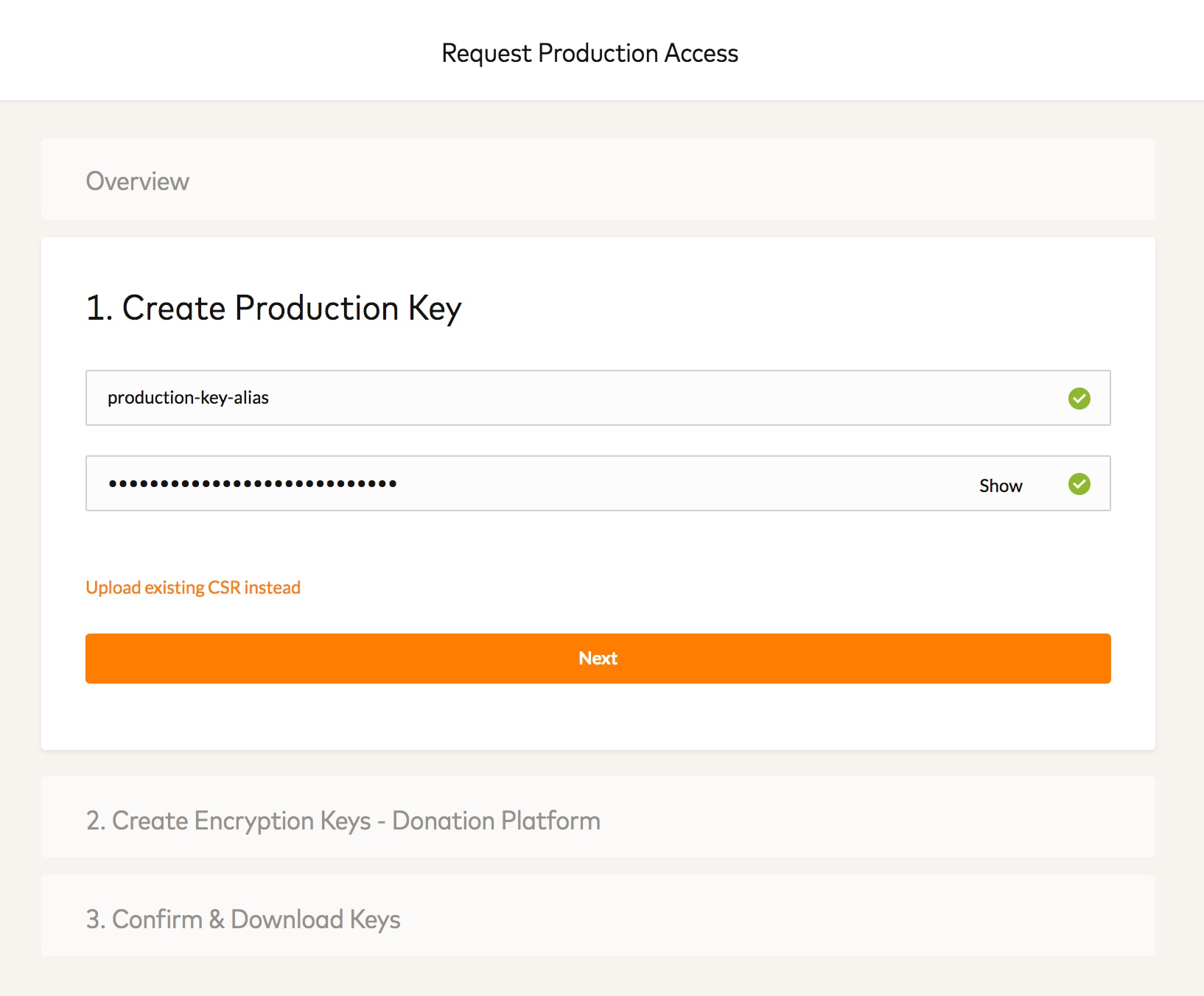
High assurance device security with CAAM encryption keys - Witekio - Experten für Embedded Systems & IoT